Links for 2019-10-20
Bye, Yahoo! Groups 🔗
Yahoo is deleting all content ever posted to Yahoo Groups (1 min, via)
I am torn between "You will not be missed" and "This is like the Geocities shutdown all over again"
In any case, this warrants an F
How to disable Linux Intel mitigations 🔗
HOWTO make Linux run blazing fast (again) on Intel CPUs
(2 min,
via)
is a quick note on the grub parameters required to make Linux faster by disabling the security mitigations
for Intel CPU bugs.
Should you do it? Benchmarks report 10%-15% performance increase with mitigations off. I have personally not taken this trade-off and my mitigations are still on, however, I have not disabled SMT which is the only 100% safe solution.
Personally, on a computer that is constantly running third party code —websites—, I prefer to lose that 15%.
Everything is louder now 🔗
Why Everything Is Getting Louder (15 min, via) blames the tech industry for the rising noise baseline we suffer everyday.
The article focuses on electronics-generated noises, but let me twist it to my agenda.
We must fight against noise pollution.
Unfortunately, in our urban modern lifestyles, we are constantly sharing our space with cars, trains, planes, ambulances, noisy cellphones, TVs, and other sources of unwanted noise.
Some things we can't avoid and, well, we just cope with them.
I hate TVs on bars, dislike ambient music, and loathe people using loud cellphones in public. I carry in-ear headphones and regularly use them even when I'm not listening to any music.
Some people just can't be alone with their thoughts and need constant external stimulus. I understand that, and can even empathize with them. But let the rest of us enjoy our moments of silence.
Both our attention and our peace of mind are precious resources, and anything that wants to deprive us of them, without good reason, is an enemy.
As I read somewhere on the Internet: "Nobody is coming to the beach to listen to their towel neighbour's music."
CO2 levels in offices 🔗
Literally Suffocating In Meetings, A Little (1 min, via) argues that high CO2 levels, which are common in poorly ventilated meeting rooms, have adverse health effects.
The NYT published a piece on CO2 levels and poor decisions, which can be summarized as "high CO2 levels make you groggy and dumb".
I guess the take home message is, watch your CO2 levels as you'd watch temperature, humidity or pollutants.
pg presents new Lisp 🔗
When one of the Lisp wizards releases a new dialect, you listen.
Of course, read the HN comments as they provide more context.
Hardware implants are becoming cheaper 🔗
Planting Tiny Spy Chips in Hardware Can Cost as Little as $200 (5 min, via) is kind of a follow-up to the infamous Bloomberg "The Big Hack" unverified piece.
In this article:
At the CS3sthlm security conference later this month, security researcher Monta Elkins will show how he created a proof-of-concept version of that hardware hack in his basement.
With only a $150 hot-air soldering tool, a $40 microscope, and some $2 chips ordered online, Elkins was able to alter a Cisco firewall in a way that he says most IT admins likely wouldn't notice, yet would give a remote attacker deep control.
Well, now we will start needing verifiable hardware, probably through other trusted hardware testing devices. This is going to be fun.
As a related note, one HN comment points out to Operation GUNMAN - how the Soviets bugged IBM typewriters which contains full details on how the bug works.
An Ode to the File 🔗
Computer Files Are Going Extinct (5 min, via) defends the usefulness of computer files and laments how we are transitioning to different metaphors in the computing world.
Most of the HN comments follow the author's thesis, but I am of a different opinion on this topic.
"Files" are difficult metaphors for most people, and they feel more comfortable when the app hides this structure behind some easier visual object.
This is just another step towards The Great Divide, which will come soon. Computing devices will be split between content creators and content consumers, and consumer devices will be absolutely different in any shape or form to creator devices.
When Steve Jobs' was interviewed at D8 (video, 2:20) where he comes up with the cars/trucks metaphors for PCs and iPads:
"When we were an agrarian nation, all cars were trucks because that's what you needed on the farms." Cars became more popular as cities rose, and things like power steering and automatic transmission became popular.
"PCs are going to be like trucks," Jobs said. "They are still going to be around." However, he said, only "one out of x people will need them."
The move, Jobs said, will make many PC veterans uneasy, "because the PC has taken us a long ways."
You are being tracked 🔗
The Fantasy of Opting Out (10 min, via) is an excellent article by two University professors on how you are being tracked online, not only with cookies and javascript, but also with your devices radios and cross-referencing datasets.
Here's the actionable part:
We can apply obfuscation in our own lives by using practices and technologies that make use of it, including:
The secure browser Tor, which (among other anti-surveillance technologies) muddles our Internet activity with that of other Tor users, concealing our trail in that of many others.
The browser plugins TrackMeNot and AdNauseam, which explore obfuscation techniques by issuing many fake search requests and loading and clicking every ad, respectively.
The browser extension Go Rando, which randomly chooses your emotional "reactions" on Facebook, interfering with their emotional profiling and analysis.
Playful experiments like Adam Harvey’s HyperFace project, finding patterns on textiles that fool facial recognition systems – not by hiding your face, but by creating the illusion of many faces.
The original Macintosh manual 🔗
Thoughts on (and pics of) the original Macintosh User Manual (10 min, via) is a beautiful review of the 1984 Mac manual, complete with high resolution pictures.

I miss printed computer manuals like the Macintoshes and the Commodores.
How to pwn 🔗
Offense At Scale (5 min, PDF) is a good intro to pentesting techniques.
I found that presentation via Defense at Scale where the author suggests strategies to reduce the attack surface.
Both presentations are good, but I liked the former best.
How file formats work 🔗
Designing File Formats (5 min, via) explains how magic numbers and file headers work.
Every programmer should know this. Go read it!
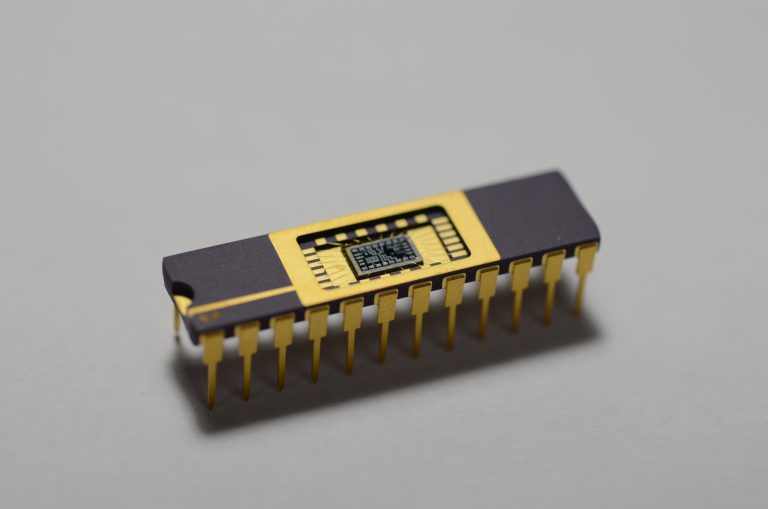
How to make an Integrated Circuit 🔗
On First IC :) (RH, via), Sam Zeloof details how he created his first "homemade" chip on his garage, from design to transistor litography.
He has some advanced machinery available, this is not really a project anybody can do "at home", but it's a very insightful read!
Tags: roundup